Mr. Brandt, already as a student you drew attention to yourself with a remarkable hack, but what led you to Fraunhofer SIT?
While I was at university, I was involved with the security of cryptoprocessors for embedded systems. As early as the 1990s, there were cashless payment systems that used such semiconductors to secure electronic money. At that time, wireless networking was not yet developed to the point that these systems would have been able to perform online verification of monetary transactions. So, the security of such systems lay primarily in cryptoprocessors. For example, that’s where users’ credit balance was stored. Then as now, breaking into such systems exerts a strong fascination over me. And so, at the time, in addition to my studies, I invested all of my free time in developing attacks on semiconductor-based security systems that were used for both eCash applications and in voting machines.
And quite successfully, too, as it turned out. How did you go about this?
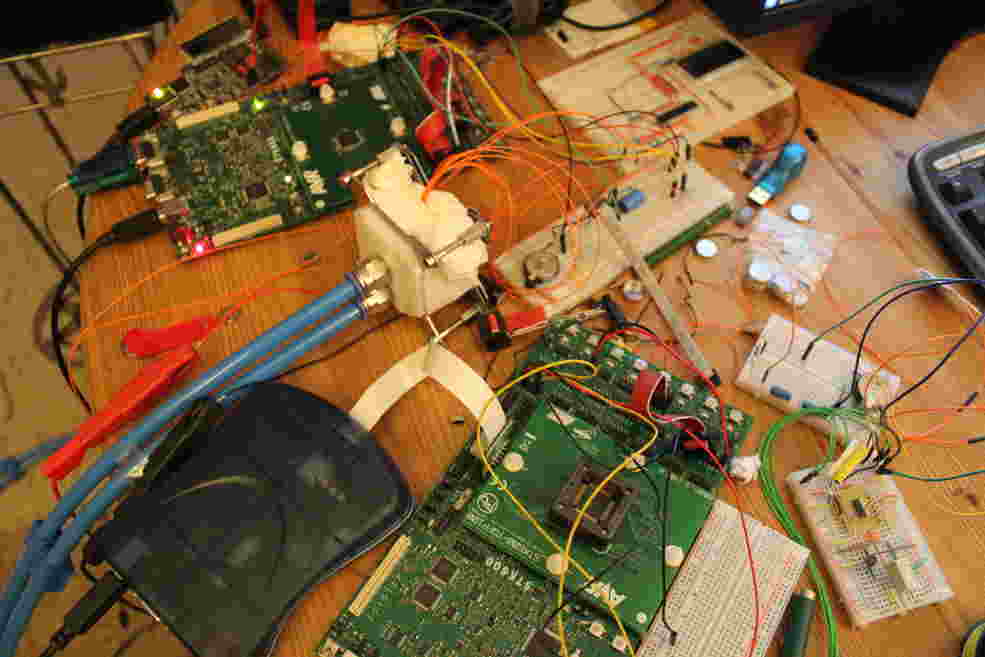
You can think of it as an iterative learning process. While the first method of attacking the chip would have taken over a hundred thousand years, the second one would have taken only two thousand years, and a few iterations later, only a few months. But that wasn’t enough for me. I kept searching for more sophisticated methods of attack. Finally, this led me to side-channel analysis. The hardware needed for this wasn’t within a student’s budget. A researcher at TU-Darmstadt gave me the crucial tip and that led me to Michael Kasper at Fraunhofer SIT.
What kind of support did you get at Fraunhofer SIT from Michael Kasper who, by the way, is now Head of Cyber- and Information Security at Fraunhofer Singapore?
Initially, I pursued this project in my own time. But as my inquiries progressed, I used them as the basis for my thesis. Michel Kasper found my project very exciting and provided me with access to the side-channel laboratory at Fraunhofer SIT. So, I continued this research as a research assistant at the Institute. It turned out that fault attacks were the key. This class of attacks uses, among other things, physical properties of semiconductors in order to provoke targeted malfunctions. By tempering the semiconductor to generate data remanence effects and the targeted use of power glitches, I was finally able to develop a differential attack with a duration of only a few seconds.
Tempering? Data remanence effects? Could you please explain that to us in more detail?
The secret key to cryptoprocessors through which all transactions are secured lies in a memory area that one can access from outside only to write, but not to read. In order for the keys to remain secret, the chip sees to it that this memory area can only be overwritten in full or not at all. By means of targeted interruption of the power supply, I was able to stop the copy process prematurely and thus to cancel out the first security feature of the semiconductor.
At normal room temperatures, this would lead to a data loss. But if you cool down a semiconductor to temperatures of -30 to -40 °C, the data are preserved for a few seconds to minutes. This phenomenon is known as the data remanence effect.
But why do you want to overwrite the unknown key? Don’t you want to find out what it is?
Exactly. But unfortunately, there was no way of directly getting at the key. The sole option would have been to read a cryptographic checksum that is calculated based on the key. One could then try out all the possible key combinations and compare them with the checksum. But there are 264 combinations – even with multiple high-speed computers, it would take many years to arrive at the solution.
In order to reduce the computing time, we overwrote the first half of the unknown key with known data. That way, we only had to try out all the combinations for the second half of the key, that is, only 232 different combinations. A modern graphic card can calculate this in less than an hour. So now we know the second half of the key, and we need only figure out the first half. For that we take a cryptographic checksum that we have generated before the first attack and that is based on the original key. Now we use the known second half of this key and only have to try out all of the possible combinations for the first half, which likewise means a maximum of 232 possible combinations. By breaking it down into two partial keys, we can reduce the calculation time exponentially. And that’s the trick to this attack. In practice, I actually even went a step further, and broke down the key into eight subkeys. That way the calculation time is reduced from 264 to 8 * 28 combinations, which brought the calculation time down to only a few milliseconds. In this way we managed to extract the secret key from the chip. And with this key it then became possible to outwit the payment systems and in fact produce as much virtual money as we wanted.
What were the consequences of this discovery?
About a year after the first publication of this weak point, the largest payment system based on this semiconductor, by the name of Akbil, which was used in Istanbul to pay for local transportation, was gone. But to date, the use of these iButtons has not yet completely disappeared. Unfortunately, the chip is still being used in security-critical areas such as voting machine systems. For me personally, the intensive engagement with this project meant that I was able to acquire a great deal of knowledge that I can now use for analyzing similar systems.
What drives someone to invest so much time in breaking into a system?
There are various reasons why someone would want to hack into a system. They can be financial or ideological. At the same time, many hackers have good intentions and want to improve the security of systems. The bigger the promises of companies, the greater the hackers’ motivation. Hackers then say: You think your system is secure? Challenge accepted! That’s a great motivator and should not be trivialized. If you want to protect yourself against hackers, you have to think like a hacker yourself. That’s why many companies also employ hackers to check the security of their own products.